Frictionless Authentication: Benefits, drawbacks, and a guide to navigating them in the second half of 2024
June 20, 2024

In 2023, global retail e-commerce sales reached a stark 5.8 trillion USD, owing to the growth of well-developed online shopping platforms and fast delivery services at affordable rates. This year, the growth is predicted to exceed 6.3 trillion USD, with leading regions being Asia, North and South America (Statista).
For e-commerce giants such as Amazon, Shopify, and Shopee, their success is largely attributed to a stable system with a wide range of merchants, a hassle-free e-commerce journey providing end-to-end customer experience. Various studies have shown that a poorly led user journey could prompt online shoppers to abandon their carts and opt for the alternatives and the payment process plays an important role.
While in Asia, there has been a surge of growth in QR code payment in the past years due to its convenience and low cost, in the America region, a large portion of the online customer pool is paying for goods with cards. These current trends in payment behavior vary country to country, with high end-user expectations for ease-of-use, prompting solution providers to design more convenient payment journeys.
In 3-D Secure 2.0, a global protocol for online customer authentication, the frictionless payment flow was introduced as a way to enhance the user experience, and at the same time ensure utmost security. Since then, the concept of a frictionless flow has been expanded and applied into different payment methods and scenarios under different names, setting the scene for more elevated payment experiences.
In this article, we will delve into frictionless authentication, their good points, limitations, and a simple guide to apply them into your payment processes in the second half of 2024.
What is frictionless authentication
Frictionless authentication is an identity verification approach that leverages on risk assessment to provide easy access to rightful credit card/ account holders while limiting risky ones. Another objective of this approach is also to minimize the need for users to further provide personal information.
In most cases, frictionless authentication is designed as a real-time process, without adding any additional steps that can be observed and experienced in the user interface. With that said, this flow of authentication relies heavily on strong risk assessment strategies and tools to ensure the right users are being let in, while suspicious ones must enter another round of authentication. Applications of this approach include account onboarding, login, or online transactions.
How does frictionless authentication work in 3-D Secure?
Within the frictionless flow, a transaction's approval depends on the 3-D Secure protocol's evaluation of various risk factors. The most basic approach of evaluation would be to apply risk-based assessments to analyze each transaction before deciding if additional authentication steps would be necessary.
Some of the factors included in 3-D Secure risk-based assessments may include:
- Transaction value
- Device information
- Transaction history
- Online behavior history
For more advanced systems to support 3-D Secure in assessing risks, other mechanisms such as AI/ Machine Learning, smart scheduling, and device intelligence further contribute to derive risk scores with higher levels of accuracy when compared to legacy systems.
Implementation of risk-based assessment mechanisms can be utilized by not only the issuer but also merchants, leveraging on the data elements to assess whether a frictionless flow or step-up authentication would prevail. Below is a diagram to indicate how an advanced fraud detection system with AI and Machine Learning risk scoring is designed to safeguard online transactions.
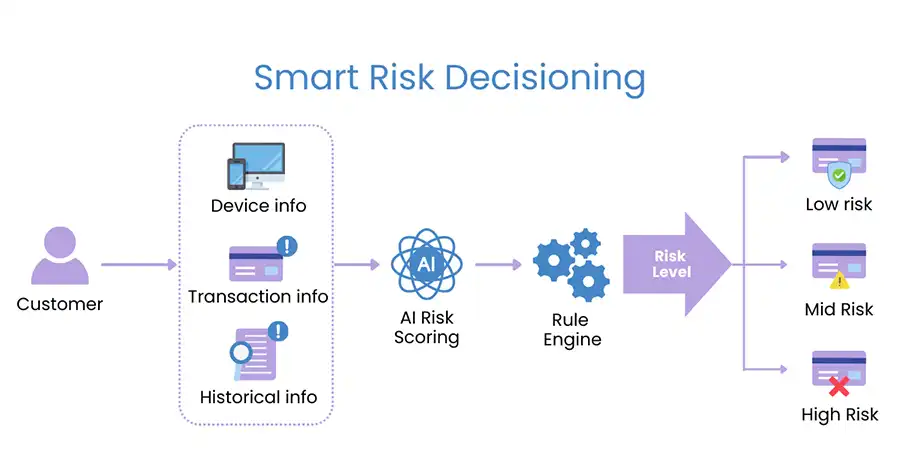
What are the other frictionless authentication techniques?
Other than the frictionless transaction flow within 3-D Secure environments, online platforms around the world have introduced different techniques to simplify and facilitate the customer journey, while retaining high security standards also categorized as frictionless means of authentication. Some of them are explained below.
Token-based authentication (authenticator mobile applications, SMS codes, OTP)
This type of authentication technique acts as a secure conduit for the transmission of user identity between applications and websites. It contributes to helping businesses bolster authentication processes for their end-users.
Using an authentication token, users on the internet can access different applications, websites, and APIs without having to enter their login credentials for every login session. After the first login, a unique token is generated and distributed among the interconnected parties (applications, websites, platforms, etc.) to authenticate the user's identity in sync.

Two of the common applications of the soft tokenization technique is Multi-factor Authentication (MFA) and Two Factor Authentication (2FA). The purpose of these two techniques are to add an extra layer onto authentication to protect user credentials from being stolen and duplicated.
Biometric authentication
In recent years, many digital banking mobile applications have been executing their frictionless revolution for online payment. The common process for this technique is to request for a biometric authentication right on the user device, if the activity (login or transaction) happens directly on the banking application. In other cases such as online payment authentication on a browser-based merchant site, the process will redirect users back to the corresponding issuer bank's mobile application for authentication using biometric.
Biometric means of authentication include fingerprint, facial recognition, iris scanning, and more. These unique traits of a user are stored within biometric authentication systems, helping the platform and service provider to authenticate the user's identity during account access.

QR Code
This type of authentication technique leverages on the “what you have” authenticating factor, in which the mobile phone will act as a token. In this approach, the platform or business will need a QR code generation mechanism to provide time-based one-time password to ensure that codes will not be replicated and re-used by bad actors.

Device Intelligence
Device Intelligence helps identify each network-connected device while gathering data about them, including device-based information such as the model, operating system, network information, and more. When applied into fraud detection and prevention strategies, thorough insight on the user devices allow 3DS transactions to be authenticated more accurately without cardholder participation. This is also a new approach that HiTRUST is currently implementing in our AI-powered Fraud Detection System - Veri-id.
Difference between frictionless flow and challenge flow
As mentioned, within the 3DS environment, customers have two different methods to verify their identity: frictionless and challenge.
The most fundamental difference between them both is that in the frictionless flow, background information is used in replacement of the need for customers to actively verify themselves as done in the challenge flow. Moreover, the SDK and servers take care of all essential information exchange, ensuring that no additional steps are required for the cardholders.
In 3DS version 1.0 and more traditional payment authentication, all transactions are processed through the challenge flow. However, this poses a major challenge for e-commerce platforms and merchants due to an increase in cart abandonment behavior. In the ever-evolving internet environment, customers are becoming more conscious about payment security, but at the same time expect a convenient shopping experience that will keep them coming back for more.
Benefits of frictionless authentication
Owing to the changes in customer preferences and fraud threats over the internet, there are certain benefits that make frictionless authentication ideal for businesses. They are:
- Enhanced customer experience: through streamlining the authentication process, a seamless experience allows for significant growth in customer satisfaction and engagement.
- Improve customer trust: a well-delivered experience positions the firm at the customer's top-of-mind and keeps them returning while eliminating other competitors or alternatives.
- Reduced cart abandonment: by simplifying the authentication process and removing unnecessary steps in the buying journey, customers are driven to make faster purchases, without abandoning the cart at the checkout phase.
- Protection against fraud: from using advanced and non-disrupting detection mechanisms, businesses can ensure a seamless payment process while deeply understanding the fraudulent risk behind each transaction.y
The challenges of frictionless authentication
Now that we understand the benefits of this convenience authentication approach, it's important to note that there are some challenges that come with it. The common ones include:
- Implementation concerns: not every frictionless payment approach is easy to implement, depending on your existing system and needs. In 3DS transactions , an issuer will not be able to implement the new payment flow without support from their solution provider.
- Ensuring compliance: each card scheme and local authority will impose different regulations on the ratio of challenge to frictionless transactions, as well as other regulations that may affect the applicable conditions.
- Troubleshooting difficulties: if your business is unfamiliar with the 3DS authentication process, it could be hard to navigate when there are technical issues. When combined with risk assessment mechanisms, 3DS transactions do get a little more complex and will require more expertise to resolve when things go wrong.
Implementing frictionless authentication on your payment system
Despite the challenges that businesses may face when implementing the frictionless flow into their payment processes, by choosing the right solution provider, you can rest assured that those concerns will not affect the system's performance.
At HiTRUST, we have been providing EMV 3DS ever since the first generation version 1.0 all the way to our latest certification for the up-coming 2.3. Owing to the strong expertise in implementing 3DS, we ensure a smooth, fully compliant solution with outstanding customer support to troubleshoot any problem that may occur.
Explore our 3DS solution, Fraud Detection System, and contact us for a detailed one-on-one consultation for your very own system.