Let's Start An Amazing Passwordless Journey!
July 20, 2024

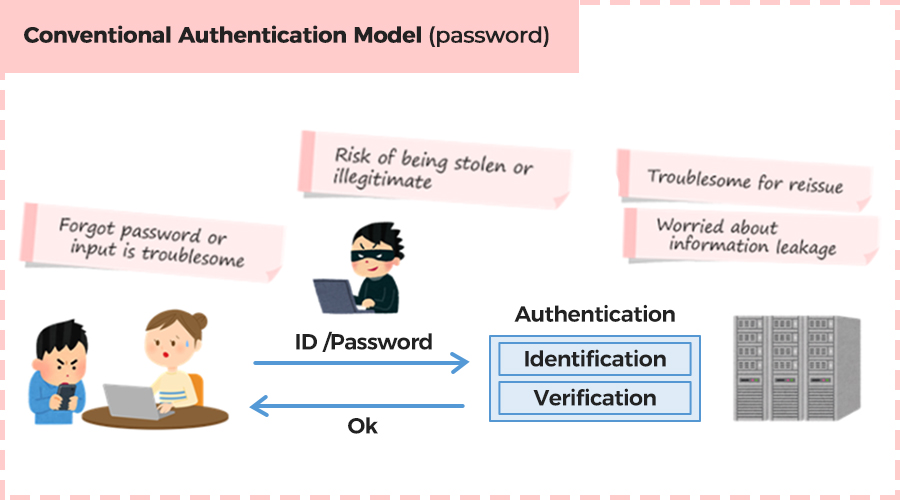
Passwords are No Longer Safe
Recently, Cybernews reported the discovery of nearly 10 billion passwords on a popular hacking forum, with the world’s most extensive compilation ever named rockyou2024.txt. This highlights a critical issue: over 33 billion passwords have been exposed, contributing to 80% of data breaches.
Password vulnerabilities grow as we increasingly live online, with the average person managing around 100 online accounts. Weak passwords and repeated combinations make accounts easy targets for hackers. Creating strong passwords for each account is not the solution since passwords are complex to remember and manage, making them not user-friendly.
Thus, It's time to explore and implement safer, more efficient authentication methods. This article will delve into advanced solutions that can protect sensitive data and ensure secure authentications.
Phase 1: Adaptive Authentication
The first step toward passwordless authentication is implementing single sign-on (SSO) and multi-factor authentication (MFA). This will standardize authentication across all applications, providing a consistent user experience and convenient control over application access. This phase includes two primary use cases.
Extended Session
Users log in with a username and password at predetermined intervals set by an administrator—such as daily, weekly, monthly, etc. During extended sessions, users' behavioral patterns will be observed, and they need to occasionally authenticate with a username and multi-factor authentication (MFA). If there are no suspicious activities, they can enjoy the passwordless experience with little input of full credentials.
This approach is similar to how users access personal or work email accounts on Gmail. In simplicity, it provides faster, more seamless experiences by reducing password prompts.
Risk-Based Authentication (RBA)
Risk-based or adaptive authentication uses policy-based risk signals to combat modern threats. It evaluates users' interactions/ behavior to enable smarter authentication decisions. Users are only prompted for multi-factor authentication (MFA) when there's elevated risk or during high-value transactions. Multiple rules help establish normal behavior baselines, and AI will detect anomalies, such as:
User Behavior Analytics: Machine learning distinguishes human behavior from bots and illegitimate users.
Device Profiling & Reputation: Identifies device characteristics and any history of fraudulent activity.
Anonymous Network Detection: Detects fraudsters using VPNs, Tor, and proxies.
IP Reputation: Blocks access from malicious domains.
Impossible Travel: Prevents logins from locations where the device couldn't have traveled since its last login.
RBA is particularly useful for customer-facing applications. For instance, if you have logged into your mobile banking app while traveling and needed an OTP or push notification, it was likely triggered by a risk score. This approach ensures user identity without friction, enhancing security and user experience.
Both methods increase user-friendliness but do not eliminate the danger of passwords. If passwords are not eliminated, fraudsters can still perform account takeovers.
Phase 2: Eliminate Passwords
Realizing that enhancing security creates more friction for users and vice versa, experts leverage the concept of MFA to eliminate passwords.
One-Time Password (OTP)
Users receive a one-time password via SMS, email, or a dedicated app. They enter this time-limit OTP to complete the authentication process. This ensures that even if the primary authentication method is compromised, the OTP provides an additional layer of security.
SMS OTPs, while enhancing security, are still vulnerable to fraud. Hackers can create fake websites to trick cardholders into entering their credentials and card details. They then use this stolen data on legitimate sites to request an OTP. Believing it's a real transaction, the cardholder provides the OTP, which the hackers use to steal funds.
Out-Of-Band (OOB)
Out-of-band (OOB) authentication uses a separate communication channel to authenticate users, adding an extra layer of security. This method ensures the authentication process remains secure even if one channel is compromised. There are various authentication methods to implement OOB:
Push-APP
Users receive a push notification on their registered mobile device application. They approve the authentication request by simply tapping the notification. This method is convenient and secure, as it requires the physical possession of the registered device.
Biometrics
Users authenticate using biometric methods such as fingerprint scans, facial recognition, or voice recognition. Biometrics provide a high level of security since they are unique to each individual and difficult to replicate.
While OOB authentication significantly enhances security, it has weaknesses. Hackers can create fake websites to trick users. Once users enter the fake website, they authenticate using OOB methods, believing they are completing a legitimate transaction. In reality, fraudsters trick users into authenticating themselves for the fraudster's malicious activities.
Email Magic Link
Another way to reduce password use is through email magic links. Users enter their username and receive an email with a link to access the desired resource. Clicking the link completes the authentication, replacing “something you know” (a password) with “something you have” (an email address).
This method is primarily used for customer identity due to the convenience of opening a link. However, it is highly vulnerable to phishing attacks, where hackers disguise themselves as legitimate operators with alternate links to steal user credentials or initiate unwanted transactions (scams).
QR Codes
QR code authentication is a valuable customer use case that saves time and reduces frustration using smartphone cameras for quick, frictionless authentication. It benefits public devices (like kiosks) or devices with limited control options. It replaces “something you know” (passwords) with “something you have” (a smartphone) and/or “something you are” (biometrics), delivering a seamless login experience that bypasses usernames and passwords.
This method can prevent password replay attacks but remains vulnerable to phishing attacks. Fraudsters can simply change the QR Code and trick users.
In short, eliminating passwords reduces the friction in authentication, but security problems, especially phishing attacks, remain. In addition, sensitive data will be stored on a public server, meaning data leakage is possible if the server is attacked.
Phase 3: FIDO Authentication
Recognizing the need for secure, user-friendly authentication, over 40 major organizations, including Microsoft, Google, and Lenovo, established the FIDO Alliance. This open standard enhances user privacy by storing biometric data on devices rather than cloud servers. With FIDO, biometric data stays on the device, avoiding the internet transmission of sensitive information.
FIDO authentication leverages public key cryptography. Users register their device's authenticator with each site or application. The authenticator generates a public/private key pair, with the public key sent to the FIDO server, ensuring only the paired device can authenticate. This not only simplifies passwordless management but also defends against phishing attacks, as fake sites can't pair with the user's device.
FIDO Authentication Methods
To complete FIDO authentication, users need a hardware device, which can be either a FIDO Security Key or a FIDO Device Authenticator:
FIDO Security Key
These hardware devices, like a YubiKey, connect to a device via USB. This method is ideal for business accounts as it supports multiple users. When visiting a registered site, the key is plugged into the computer, and a fingerprint scan (if needed) completes the authentication.
FIDO Device Authenticator
This method utilizes built-in device biometrics, such as fingerprint or facial recognition on your phone, eliminating the need to carry extra hardware. There are two primary methods within this category:
Universal Authentication Framework (UAF): It prompts for biometric factors like fingerprints or facial scans, limited to native applications with one key per account.
Passkeys: It is implemented on browsers and applications, working across devices within the same ecosystem, like Apple's iCloud Keychain or Google's Smart Lock.
HiTRUST Supports Passwordless Authentication
With 25 years of experience securing online payments, we believe that FIDO will soon become the industry standard for authentication. Whether for login or transactions, FIDO is poised to be the go-to authentication method. That's why we built our authentication solution, Veri FIDO, based on the FIDO Alliance standard. Since 2021, HiTRUST has been certified for FIDO UAF and FIDO2. Moreover, we offer an optional package to collect up to 100 additional behavioral metrics to further enhance our clients' protection.
Conclusion
The journey towards passwordless authentication involves multiple phases, starting with adaptive authentication and moving towards eliminating passwords with advanced methods like FIDO. While each phase presents challenges and vulnerabilities, the ultimate goal is to provide a secure, user-friendly authentication process that significantly reduces the risk of credential theft and phishing attacks. HiTRUST is committed to supporting this transition with our robust Veri FIDO solution, ensuring that banking and financial institutions can offer their customers the highest level of security.





